Use CoreOS Container Linux on Linode
CoreOS Container Linux is a container-focused distribution, designed for clustered deployments, that provides automation, security, and scalability for applications. The operating system is heavily streamlined and considered minimal compared to traditional distributions, like Debian or Ubuntu. Rather than being part of the host operating system, CoreOS’s runtime or development environment takes place inside a Linux container.
Container Linux supports running Docker, Kubernetes and rkt container environments.


Container Linux Configuration Profile
When you deploy a Container Linux image, you’ll notice the default settings in the configuration profile are different from those of other distributions.
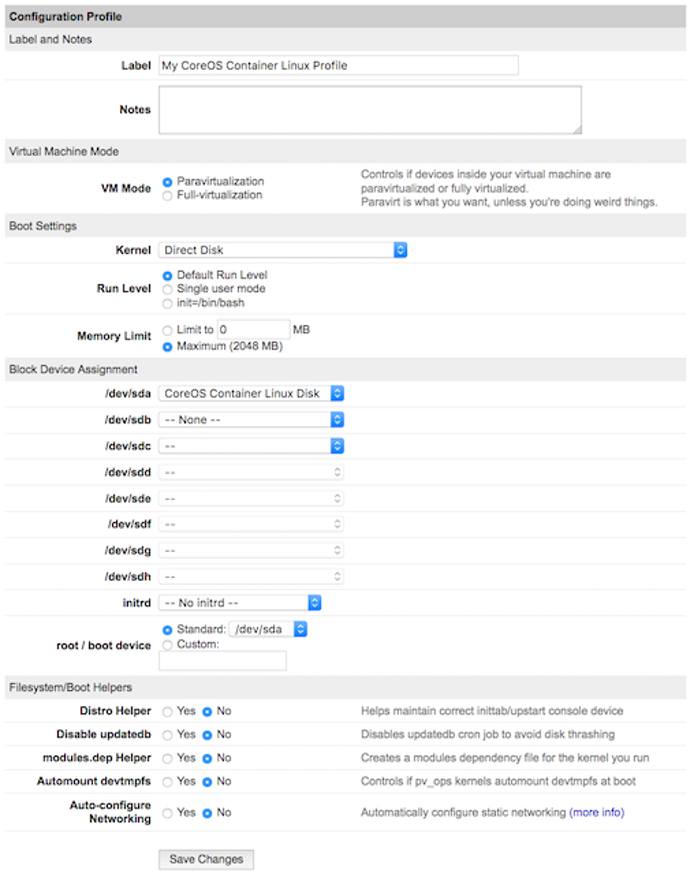
Boot Settings
Container Linux boots with the Direct Disk setting as opposed to GRUB2 or any other. Container Linux is not compatible with the Linode kernels.
Block Device Assignment
Container Linux does not use a swap space, so while Linode’s other distributions use /dev/sdb as a swap area, this is not necessary with Container Linux.
Filesystem/Boot Helpers
These are not needed for Container Linux, and Network Helper is not compatible so they are all disabled. Linode’s Container Linux images use systemd-networkd, so see our
static networking guide if you want to configure static and/or multiple IP addresses for your deployment.
NoteThe Linode backup service is not available for Container Linux. You should back up your data and configurations using an alternative backup method.
Log into Container Linux
The default user is the core user, so you must log in as core rather than root. The root user does not have a password assigned to it by default. This is the intended use of Container Linux.
Container Linux Updates and Reboot Strategies
Container Linux has no package manager such as apt or yum, and in fact the operating system is not upgraded with individual package updates like most distributions. Instead, entire system updates are pushed to the distribution and the system reboots in accordance with one of three reboot strategies.
The default configuration is to follow the etcd-lock strategy if etcd is being used (such as if you are clustering Linodes running Container Linux). If not, the system will reboot immediately after applying the update. For the Linode to boot back up automatically, you will want Lassie enabled in the Linode Manager.
If you find an update has undesirable effects, roll back to the previous version you were using. Update checks will take place about 10 minutes after Container Linux boots and about every hour afterwards. Should you need to trigger a manual update, use:
update_engine_client -check_for_update
Recovery Mode
Should you need to access your Container Linux disk using Rescue Mode, use the boot instructions shown in our
Rescue and Rebuild guide. The root partition is located on /dev/sda9. To access it, enter:
mount /dev/sda9 && cd /media/sda9
That will put you at the root of your Container Linux filesystem. For more information on the partition layout of Container Linux, see the Container Linux Disk Partitions Guide.
This page was originally published on






